The building blocks of control
Four building blocks
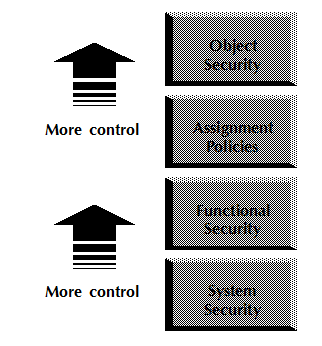
There are four major “building blocks” of security control. All are required to effectively use 25Live.
• System security
• Functional security
• Assignment policies
• Object security
In addition to these, you can define notification policies. See
“Notification Policies”System Security
System security controls access to the 25Live application. Access is limited to “active” 25Live users via unique user ID and password. System security is the most basic building block of control in 25Live.
Functional Security
Functional security controls access to functional areas of 25Live, such as whether or not a user can access the event search function or run reports. Functional security is the most basic building block of usage control in 25Live.
Assignment Policies
Assignment policies control for each location and resource who can assign it to events and when it can be assigned to events.
Object Security
Object security controls access to individual events, event drafts, locations, resources, organizations, cabinets, folders, and reports, and, for locations and resources, the events they’re assigned to.
The building blocks build on each other
Security “building blocks” build upon each other, each providing an additional level of control.